Sp00kyCTF 2023
Putting on the third annual Sp00kyCTF by IASG at Iowa State University
This year was the third annual SpookyCTF put on by the Information Assurance Student Group here at Iowa State University. This CTF is designed to be an introduction to Capture The Flag competitions as whole, to allow students here at Iowa State have an way to learn more and take part in a CTF with having minimal or no knowledge, and have fun while doing it. Part of how we make it beginner friendly is by having the cabinet create challenges for the competition, we were in the same seats as the participants not that long ago, and gives us a good perspective on what we would know in their shoes.
Now that the competition is couple weeks behind me, I’m taking some time to reflect on how the competition went. On the immediate day of the competition, I thought it went extremely, with no major issues happening, and good participation. What made me more proud, was both during and after competition, participating students talked about how they enjoyed the competition, and how they felt like they learned things by competing. This alone makes the whole event a success to me, younger students getting helped into that baseline knowledge level to be able to compete on their own in CTFs in the future, and having fun while doing it.
The participants were not the people learning from the event though, I also learned a lot from this event as well. Something that was new this year was that we had sponsors for the event and not purely club funded. As the club really has not done large amounts of fundraising, getting donations from corporations was a new experience for me. I decided to reach out to RSM about sponsoring prizes, as their funding would allow our club to provide better overall prizes for the participants. After reaching out to a contact that I had there, they were more than happy to help, and provided the prizes for the first place team.
We also were reached out to by SecDSM, a local cyber security group, about helping with the event when they heard that we were putting it on. They wanted to also help with prize and food support, which was amazing! They provided the second place prizes, along with lunch for all the participants. What was more unexpected is that I also mentioned that if there was anyone looking to create some challenges for the event, that we would be interested in having them help out there too.
To my surprise, there was someone that was interested in helping out with making challenges. This person was a long time veteran CTF player, and also helped create a number of CTFs before. This was a wonderful learning experience for me to have someone experienced helping with the competition, as he firstly in just a couple days filled out many of the beginner level challenges that we knew we wanted to make, but had not completed yet, along with adding many of his own. The part that I learned the most from, was how to weight and balance challenges, points, and hints, so that the competition was fair and fun. While we had been trying to balance these already, that was one of the struggles from competition last year with challenges not being weighted correctly. Having him guide me on how to score challenges well against each other, so that one category, or challenges made by one person were worth more than others, was a great learning experience for me.
For the competition, I also had the chance to write a total of 17 challenges. I had written a few small challenges before, but this year I set out to write some hardware based challenges, since that often feels under represented in CTFs, and hardware security is a passion of mine. Of the 17 challenges that I ended up writing 4 hardware based challenges total, all of which turned out very well and covered a very broad range of difficulty. My favorite of the challenges has to be a challenge called RGB Madness which gave the users a capture from a logic analyzer that was taken while capturing the output of a micro-controller powering an array of LEDs. With the default view showing just a few points, but as you zoomed in there was a lot more noticeable detail about each of the locations with peaks.
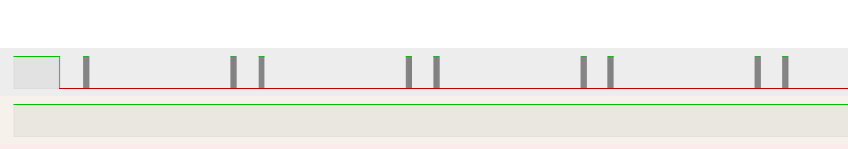 The wide view of the logic analyzer capture, that shows a few areas with peaks, but not major detail.
The wide view of the logic analyzer capture, that shows a few areas with peaks, but not major detail.
 Zooming in on one of the peaks to show how each sections has clear detail about what is happening on the wire.
Zooming in on one of the peaks to show how each sections has clear detail about what is happening on the wire.
There some information that this was using a common RGB LED based on everything that was known. In this case, this signalling is using the protocol for the WS2812B LED, which is a common LED used in many projects. The protocol is a relatively simple one with a “packet” containing 3 bytes * number of LEDs, where each byte represents the R, G, and B values specifically. And each bit of the packet either being represented by a “long” pulse where 2/3 of the pulse time is high representing a 1, and a “short” pulse where 1/3 of the pulse is high representing a 0, then constant low when no data transmission is happening. Being this simple there were a variety of ways to decode it, either with a program or by hand. The challenge used either white or off for LEDs, so the 3 byte values in each packet were either all 0s or all 1s, which made it easy to see the difference between a 0 and 1. This could then be decoded by hand with a sliding scale the length of a packet and reading if the LED was on or off at each point. It could have also been automated in a variety of ways like using a decoder built into a logic analyzer.
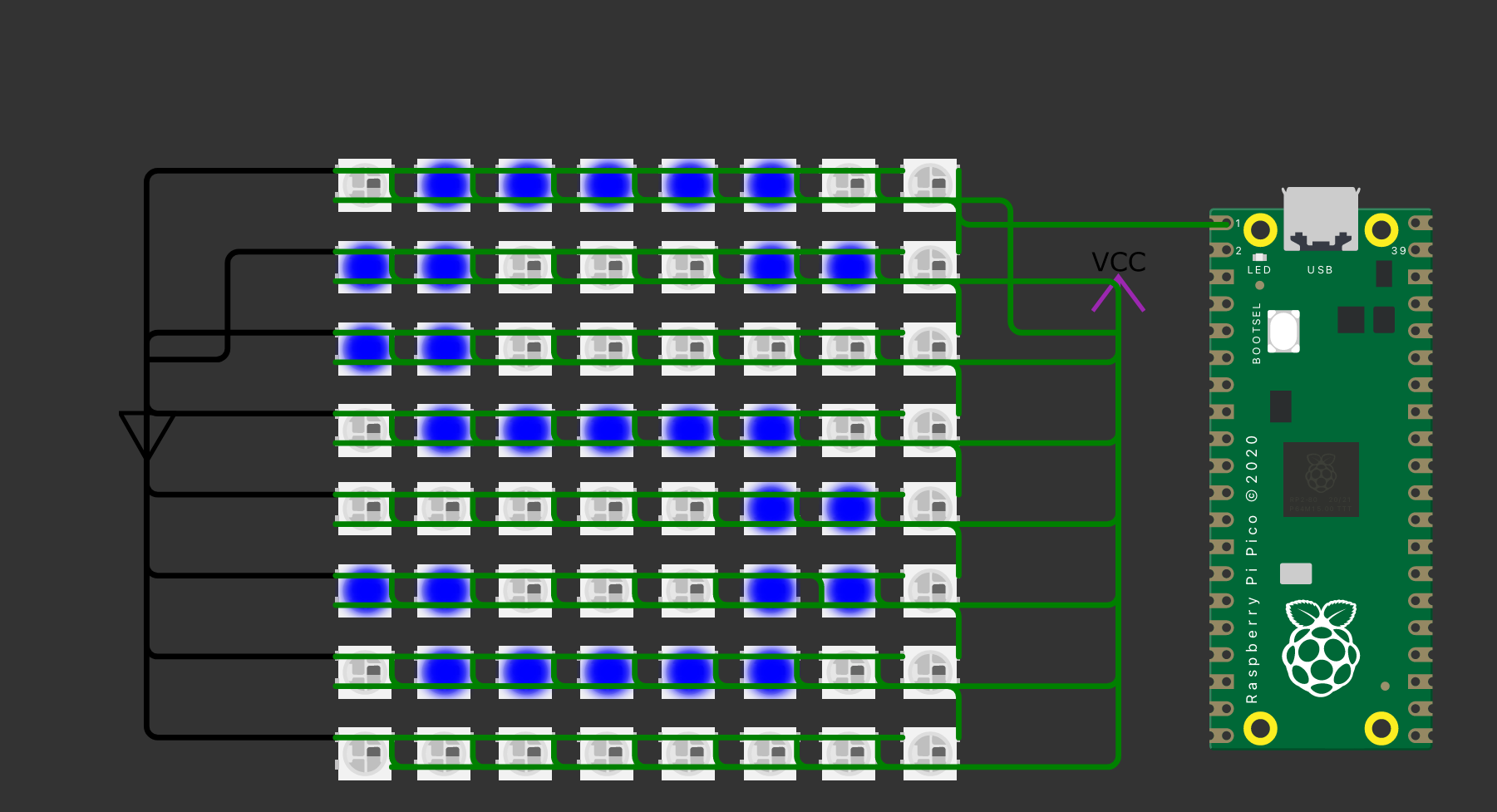 Image showing the letter ‘S’ would appear on the LEDs in on online micro-controller simulator. In this case I used blue, since it showed up better in this online simulator.
Image showing the letter ‘S’ would appear on the LEDs in on online micro-controller simulator. In this case I used blue, since it showed up better in this online simulator.
This challenge was a lot of fun to make as it helped me build my skills in using a logic analyzer to capture data from real hardware, along with working with micro-controller modeling tools like Wokwi where I built an basic testing LED array, so that I could test my code without having to utilize real hardware. Wokwi Testing Environment.